I posted something similar to this a while back but the intent of that post was to show how you could specify certain URL's and then drop everything else. That is sort of an odd setup so I thought I would try and document something a little more common.
• In this design we are turning on http inspection and then calling out a few web sites with regular expressions and then based on a match dropping that connection - simple. Because class-maps and policy-maps match statement are so nested and a little confusing to decipher I have laid out exactly what is being done to make all this work.
• Step 1 - The first thing we are doing is defining the regular expressions. You give them a name and you add in the FQDN
• Step 2 - The next step is to create a regular expression class map called blacklist and add in a match statement that points back at the regular expressions you defined a step ago. If later on you decide to add more sites to this "forbidden list" then you would create them as you did in step 1 and then add then under the class map you just created here in step 2.
• Step 3 - Now we're ready to enter some intelligence into this setup. The key to this step is the "match request header" portion. This tells the ASA that you want to match the http header with the regular expressions you defined - they're referenced as class "blacklist" from step 2.
• Step 4 - Here we create a policy-map called black-regex. This is simply the action you want to take after all the criteria are met. In this case it's drop-connection.
• Step 5 - Now we define the global policy (if one does not already exist on the ASA) and the statement class inspection_default will get you a bunch of other inspections that you may or may not want - the one we care about is defined as inspect http and then we reference black-regex.
• Step 6 - This is the most important step in the process. Here we put all of this into action by allying it on an interface. Since we are attempting to stop people from the inside from going to these sites we apply it there.
This could be seen as the poor network engineers web filter or a way to kill youtube the next time a celebrity dies and the entire office decides to suck up every last bit of available bandwidth...
Here are the commands in the illustration laid out for you to copy:
regex forbid1 "xxy.com"
regex forbid2 "xxy.com"
!
class-map type regex match-any BLACKLIST
match regex forbid1
match regex forbid2
!
class-map type inspect http match-all BLACKMAP
match request header host regex class BLACKLIST
!
policy-map type inspect http BLACK-REGEX
parameters
class BLACKMAP
drop-connection
!
policy-map global_policy
class inspection_default
inspect http BLACK-REGEX
!
service-policy global_policy [interface or global]
Happy filtering!
Thursday, December 2, 2010
Thursday, November 25, 2010
basic commands for snmpwalk
The concept of snmpwalk is very simple. All you are doing is asking a remote device that has an snmp string configured about a particular MIB. In the case of this example I am asking an IPS about it's operational status and it's interfaces. As long as you are allowed access to request the information (in the case of the IPS I specifically allowed the workstation I am requesting the information from) you should have no problem.
• From a unix box you would issue the following:
snmpwalk [the version of snmp it's running]
-c [the snmp sting you configured for read only access]
[the ip address of the remote device]
[the information being requested] You can get a listing of supported MIB's here
• It ends up looking something like this:
host$ snmpwalk -v2c -c public x.x.x.x ifOperStatus
- This is the output that you get for the operational status request:
IF-MIB::ifOperStatus.1 = INTEGER: up(1)
IF-MIB::ifOperStatus.2 = INTEGER: up(1)
IF-MIB::ifOperStatus.3 = INTEGER: up(1)
IF-MIB::ifOperStatus.4 = INTEGER: up(1)
IF-MIB::ifOperStatus.5 = INTEGER: down(2)
• Same thing for an interface description request:
host$ snmpwalk -v2c -c public x.x.x.x ifDescr
IF-MIB::ifDescr.1 = STRING: lo
IF-MIB::ifDescr.2 = STRING: eth0
IF-MIB::ifDescr.3 = STRING: sy0_0
IF-MIB::ifDescr.4 = STRING: ma0_0
IF-MIB::ifDescr.5 = STRING: ge0_0
• And another output from the interface admin status
host$ snmpwalk -v2c -c public x.x.x.x ifAdminStatus
IF-MIB::ifAdminStatus.1 = INTEGER: up(1)
IF-MIB::ifAdminStatus.2 = INTEGER: up(1)
IF-MIB::ifAdminStatus.3 = INTEGER: up(1)
IF-MIB::ifAdminStatus.4 = INTEGER: up(1)
IF-MIB::ifAdminStatus.5 = INTEGER: down(2)
Happy querying!
• From a unix box you would issue the following:
snmpwalk [the version of snmp it's running]
-c [the snmp sting you configured for read only access]
[the ip address of the remote device]
[the information being requested] You can get a listing of supported MIB's here
• It ends up looking something like this:
host$ snmpwalk -v2c -c public x.x.x.x ifOperStatus
- This is the output that you get for the operational status request:
IF-MIB::ifOperStatus.1 = INTEGER: up(1)
IF-MIB::ifOperStatus.2 = INTEGER: up(1)
IF-MIB::ifOperStatus.3 = INTEGER: up(1)
IF-MIB::ifOperStatus.4 = INTEGER: up(1)
IF-MIB::ifOperStatus.5 = INTEGER: down(2)
• Same thing for an interface description request:
host$ snmpwalk -v2c -c public x.x.x.x ifDescr
IF-MIB::ifDescr.1 = STRING: lo
IF-MIB::ifDescr.2 = STRING: eth0
IF-MIB::ifDescr.3 = STRING: sy0_0
IF-MIB::ifDescr.4 = STRING: ma0_0
IF-MIB::ifDescr.5 = STRING: ge0_0
• And another output from the interface admin status
host$ snmpwalk -v2c -c public x.x.x.x ifAdminStatus
IF-MIB::ifAdminStatus.1 = INTEGER: up(1)
IF-MIB::ifAdminStatus.2 = INTEGER: up(1)
IF-MIB::ifAdminStatus.3 = INTEGER: up(1)
IF-MIB::ifAdminStatus.4 = INTEGER: up(1)
IF-MIB::ifAdminStatus.5 = INTEGER: down(2)
Happy querying!
Wednesday, November 24, 2010
Upgrading ASA 5505 Memory and Flash
This post is focusing on the upgrade process for the ASA 5505 from version 8.2 to 8.3. The new code requires more memory and so you will need to crack the box open and pull out the existing memory module and if you want, the compact flash module as well.
The process is very easy, just flip it over and pop the tree screws loose (pull the sides apart and lift up and the cover should come right off). The next step is to pull the memory module out and replace it - super easy and you can watch someone do it on youtube here.
Now comes the hard part - upgrading the compact flash. You would think you could pull the existing flash card out of the slot (the one that the cover was obscuring) and place the new one in the slot, power it up and dump into RMON and erase it - like this:.
rommon #1> erase ?
Erase storage media, valid for this platform:
disk0: - erase this device
all - erase all devices listed above
!
rommon #1> erase disk0:
About to erase the selected device, this will erase
all files including configuration, and images.
Continue with erase? y/n [n]: y
Erasing Disk0:
.................................................
Then all you would need to do is connect the old compact flash card to a USB reader and pull the files off the old one (remember to get the hidden directories) and then copy those onto the new card....
• Nope. The card once formatted by the ASA is unreadable in a PC. The format that is required is Microsoft FAT 16.
Going back to the PC and the unreadable flash card - format the card to the correct type and then copy over the files and clean things up a bit. It should look something like this when you list all the files from a PC:
drwxrwxrwx 816 Nov 24 22:56 .
drwxr-xr-x 136 Nov 24 22:56 ..
!
<---- .private is where all the magic files are stored
drwxrwxrwx 408 May 6 2008 .private
!
-rwxrwxrwx 15962112 Nov 20 2010 asa832-k8.bin
-rwxrwxrwx 16275456 May 11 2009 asa821-k8.bin
!
-rwxrwxrwx 14503836 Nov 20 2010 asdm-634.bin
-rwxrwxrwx 11348300 May 11 2009 asdm-621.bin
!
drwxrwxrwx 102 May 11 2009 coredumpinfo
drwxrwxrwx 68 May 6 2008 crypto_archive
• Now take that freshly loaded new flash card and place it into the ASA and boot it up.
Good luck!
The process is very easy, just flip it over and pop the tree screws loose (pull the sides apart and lift up and the cover should come right off). The next step is to pull the memory module out and replace it - super easy and you can watch someone do it on youtube here.
Now comes the hard part - upgrading the compact flash. You would think you could pull the existing flash card out of the slot (the one that the cover was obscuring) and place the new one in the slot, power it up and dump into RMON and erase it - like this:.
rommon #1> erase ?
Erase storage media, valid
disk0: - erase this device
all - erase all devices listed above
!
rommon #1> erase disk0:
About to erase the selected device, this will erase
all files including configuration, and images.
Continue with erase? y/n [n]: y
Erasing Disk0:
.................................................
Then all you would need to do is connect the old compact flash card to a USB reader and pull the files off the old one (remember to get the hidden directories) and then copy those onto the new card....
• Nope. The card once formatted by the ASA is unreadable in a PC. The format that is required is Microsoft FAT 16.
Going back to the PC and the unreadable flash card - format the card to the correct type and then copy over the files and clean things up a bit. It should look something like this when you list all the files from a PC:
drwxrwxrwx 816 Nov 24 22:56 .
drwxr-xr-x 136 Nov 24 22:56 ..
!
<---- .private is where all the magic files are stored
drwxrwxrwx 408 May 6 2008 .private
!
-rwxrwxrwx 15962112 Nov 20 2010 asa832-k8.bin
-rwxrwxrwx 16275456 May 11 2009 asa821-k8.bin
!
-rwxrwxrwx 14503836 Nov 20 2010 asdm-634.bin
-rwxrwxrwx 11348300 May 11 2009 asdm-621.bin
!
drwxrwxrwx 102 May 11 2009 coredumpinfo
drwxrwxrwx 68 May 6 2008 crypto_archive
• Now take that freshly loaded new flash card and place it into the ASA and boot it up.
Good luck!
Friday, August 13, 2010
Injecting a default route into OSPF
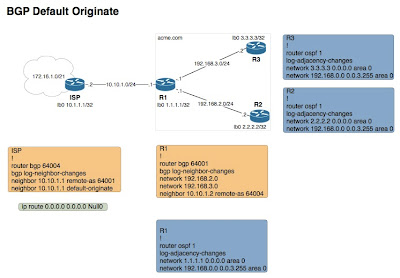
This post will build off the BGP Basics post that I did earlier this month. Here is what we are looking to achieve this time:
• The ISP router will advertise a default route to his neighbor R1 (acme.com's internet gateway)
• R1 will then advertise to R2 and R3 via OSPF the default route
• R2 and R3 will be able to access the 172.16.1.0/21 network even though they have no specific route to this network
Here we go:

• Starting with the ISP router, we are going to remove the default route that we added in on the last post
ISP#
!
no ip route 0.0.0.0 0.0.0.0 Null0
We still have the default-originate statement under the router bgp 64004 statement so we should be good. Over on R1 we should see that he has an entry that looks like this:
R1#
!
show ip route
!
B* 0.0.0.0/0 [20/0] via 10.10.1.2, 00:16:27
• Next we are going to look at R2 and R3 to see what routes they have. They should look something like this (taken from R2)

• On R1 we are going to add a statement to the OSPF process that will advertise the default route.
R1#
!
router ospf 1
!
default-information originate
On R2 and R3 we see this entry for the default route and we also see a gateway of last resort set (from R2):

• Now if we were to go back to the ISP router and pull the default-originate statement from BGP (or down the serial 0/0 interface) what do you think we will see on R1?
- Answer: R1 will no longer have a route to 0.0.0.0 from the ISP router. Because of this R2 and R3 have lost their default route and gateway of last resort. The reason for this is because the route will not be advertised to other OSPF neighbors unless it's in R1's table.
Now that we have established this we can restore the default route and test the theory that we can reach things from R2 and R3 that are not in their route table.
• The network 172.16.3.0 exists off the ISP router and specifically 172.16.3.1. If we ask R2 about this network is tells us it has no idea what we are talking about:
R2#show ip route 172.16.3.1
% Network not in table
When we ping it here is what we see:
R2#ping 172.16.3.1
!
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/30/44 ms
A traceroute shows that it gets to the ISP router just fine:
R2#traceroute 172.16.3.1
!
Tracing the route to 172.16.3.1
1 192.168.2.1 24 msec 20 msec 20 msec
2 10.10.1.2 24 msec * 20 msec
[stop]
• The ISP router will advertise a default route to his neighbor R1 (acme.com's internet gateway)
• R1 will then advertise to R2 and R3 via OSPF the default route
• R2 and R3 will be able to access the 172.16.1.0/21 network even though they have no specific route to this network
Here we go:

• Starting with the ISP router, we are going to remove the default route that we added in on the last post
ISP#
!
no ip route 0.0.0.0 0.0.0.0 Null0
We still have the default-originate statement under the router bgp 64004 statement so we should be good. Over on R1 we should see that he has an entry that looks like this:
R1#
!
show ip route
!
B* 0.0.0.0/0 [20/0] via 10.10.1.2, 00:16:27
• Next we are going to look at R2 and R3 to see what routes they have. They should look something like this (taken from R2)

• On R1 we are going to add a statement to the OSPF process that will advertise the default route.
R1#
!
router ospf 1
!
default-information originate
On R2 and R3 we see this entry for the default route and we also see a gateway of last resort set (from R2):

• Now if we were to go back to the ISP router and pull the default-originate statement from BGP (or down the serial 0/0 interface) what do you think we will see on R1?
- Answer: R1 will no longer have a route to 0.0.0.0 from the ISP router. Because of this R2 and R3 have lost their default route and gateway of last resort. The reason for this is because the route will not be advertised to other OSPF neighbors unless it's in R1's table.
Now that we have established this we can restore the default route and test the theory that we can reach things from R2 and R3 that are not in their route table.
• The network 172.16.3.0 exists off the ISP router and specifically 172.16.3.1. If we ask R2 about this network is tells us it has no idea what we are talking about:
R2#show ip route 172.16.3.1
% Network not in table
When we ping it here is what we see:
R2#ping 172.16.3.1
!
Sending 5, 100-byte ICMP Echos to 172.16.3.1, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 20/30/44 ms
A traceroute shows that it gets to the ISP router just fine:
R2#traceroute 172.16.3.1
!
Tracing the route to 172.16.3.1
1 192.168.2.1 24 msec 20 msec 20 msec
2 10.10.1.2 24 msec * 20 msec
[stop]
Friday, August 6, 2010
BGP Basics
I have long admitted that I am not a BGP expert and so I will try my best get better with it over the course of the next few blogs related to configuration and redistribution.
• The example I am working with today is a very basic setup with an ISP router and three routers inside what we will call the acme.com network. The ISP router is in AS 64004 and has a default route which it will be advertising into R1 at acme. The R1 router will be running BGP AS 64001 and the two will be defined as neighbors.
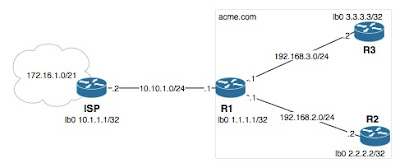
Here is what is needed to make this work:
ISP#
!
router bgp 64004
neighbor 10.10.1.1 remote-as 64001
R1#
!
router bgp 64001
neighbor 10.10.1.2 remote-as 64004
• With that basic information entered in we should see the neighbors form and a "show ip bgp summary" on the ISP router will show you this:
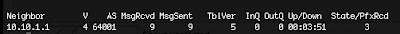
• The next part of this is to get the networks that connect from R1 to R2 and R3 (192.168.2.0/24 and 192.168.3.0/24) advertised to the ISP router. First we need to get them into OSPF and this is what needs to be placed into R1, R2, and R3:
Rx#
!
router ospf 1
log-adjacency-changes
network [IP of the loopback interface of the router] area 0
network 192.168.0.0 0.0.3.255 area 0
This will get you adjacency between all three routers. Something like this (shown from R3's perspective):
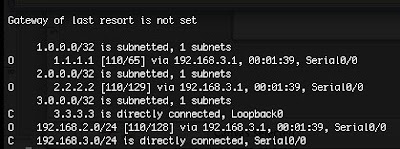
• Now on the R1 router we add in the network statements under the BGP process for the 192.168.2.0 and 192.168.3.0 networks
R1#
!
router bgp 64001
network 192.168.2.0
network 192.168.3.0
!
The ISP router should now see the two networks:
ISP# show ip route
!
B 192.168.2.0/24 [20/0] via 10.10.1.1, 00:00:21
B 192.168.3.0/24 [20/0] via 10.10.1.1, 00:00:22
• Now lets create a default route on the ISP router (in this case to null 0)
ISP#
!
ip route 0.0.0.0 0.0.0.0 Null0
• Now lets advertise that route to our neighbor R1 at 10.10.1.1
ISP#
!
router bgp 64004
neighbor 10.10.1.1 default-originate
On the R1 router we now see the a default route learned via BGP
R1# show ip route
!
B* 0.0.0.0/0 [20/0] via 10.10.1.2, 03:07:04
• This is the final result. A very simple network design that we will continue to modify over the next few blogs:
• The example I am working with today is a very basic setup with an ISP router and three routers inside what we will call the acme.com network. The ISP router is in AS 64004 and has a default route which it will be advertising into R1 at acme. The R1 router will be running BGP AS 64001 and the two will be defined as neighbors.

Here is what is needed to make this work:
ISP#
!
router bgp 64004
neighbor 10.10.1.1 remote-as 64001
R1#
!
router bgp 64001
neighbor 10.10.1.2 remote-as 64004
• With that basic information entered in we should see the neighbors form and a "show ip bgp summary" on the ISP router will show you this:

• The next part of this is to get the networks that connect from R1 to R2 and R3 (192.168.2.0/24 and 192.168.3.0/24) advertised to the ISP router. First we need to get them into OSPF and this is what needs to be placed into R1, R2, and R3:
Rx#
!
router ospf 1
log-adjacency-changes
network [IP of the loopback interface of the router] area 0
network 192.168.0.0 0.0.3.255 area 0
This will get you adjacency between all three routers. Something like this (shown from R3's perspective):

• Now on the R1 router we add in the network statements under the BGP process for the 192.168.2.0 and 192.168.3.0 networks
R1#
!
router bgp 64001
network 192.168.2.0
network 192.168.3.0
!
The ISP router should now see the two networks:
ISP# show ip route
!
B 192.168.2.0/24 [20/0] via 10.10.1.1, 00:00:21
B 192.168.3.0/24 [20/0] via 10.10.1.1, 00:00:22
• Now lets create a default route on the ISP router (in this case to null 0)
ISP#
!
ip route 0.0.0.0 0.0.0.0 Null0
• Now lets advertise that route to our neighbor R1 at 10.10.1.1
ISP#
!
router bgp 64004
neighbor 10.10.1.1 default-originate
On the R1 router we now see the a default route learned via BGP
R1# show ip route
!
B* 0.0.0.0/0 [20/0] via 10.10.1.2, 03:07:04
• This is the final result. A very simple network design that we will continue to modify over the next few blogs:

Wednesday, February 3, 2010
Call Manager Express over an IPSec Tunnel
This one isn't going to be easy to explain in just text so lets looks at the picture of the network first:

This design has a bunch of technologies mixed into it so I have laid out the goals and the configuration that supports the design.
• #1 Bring up a 2811 named Chico running Advanced IP Services 12.4(15) T9 and hang a WAN connection off it - using either a static IP, or DHCP given address, both option will be shown.
11 -rw- 51432612 May 22 2009 07:17:46 -07:00 c2800nm-advipservicesk9-mz.124-15.T9.bin
interface FastEthernet0/0
ip address 192.168.100.1 255.255.255.252
duplex auto
speed auto
• #2 Configure DHCP and option 150 on Chico to show the devices (phones) where the Call Manager Express (CME) lives.
ip dhcp pool VOICE
network 172.16.100.0 255.255.255.0
option 150 ip 162.2.245.1
default-router 172.16.100.1
ip dhcp excluded-address 172.16.100.1
• #3 Configure a PoE switch with a voice vlan for the phones to hang off and uplink that to Chico via a trunk.
chico#
interface FastEthernet0/1.2
encapsulation dot1Q 2
ip address 172.16.100.1 255.255.255.0
• #4 Build a WAN between Chico and a 2801 named Redding and load Advanced IP Services 12.4(15) T7 and the appropriate CME files into its flash.
chico#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 192.168.100.0 0.0.0.3 area 1
sacramento#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 10.10.1.4 0.0.0.3 area 0
yolo#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 10.10.1.4 0.0.0.3 area 0
network 192.168.100.0 0.0.0.3 area 1
redding#
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
- Files in Redding's Flash. Not sure all this stuff is needed but here's the mess:
1 10035 Feb 1 2010 18:06:10 -08:00 CME41-basic-readme.txt
2 0 Feb 1 2010 18:06:10 -08:00 gui
3 4802 Feb 1 2010 18:06:12 -08:00 gui/admin_user.html
4 657587 Feb 1 2010 18:06:16 -08:00 gui/admin_user.js
5 1602 Feb 1 2010 18:06:16 -08:00 gui/CiscoLogo.gif
6 716 Feb 1 2010 18:06:16 -08:00 gui/CME_GUI_README.TXT
7 953 Feb 1 2010 18:06:16 -08:00 gui/Delete.gif
8 16344 Feb 1 2010 18:06:18 -08:00 gui/dom.js
9 864 Feb 1 2010 18:06:18 -08:00 gui/downarrow.gif
10 6146 Feb 1 2010 18:06:18 -08:00 gui/ephone_admin.html
11 4658 Feb 1 2010 18:06:18 -08:00 gui/logohome.gif
12 3724 Feb 1 2010 18:06:18 -08:00 gui/normal_user.html
13 81443 Feb 1 2010 18:06:20 -08:00 gui/normal_user.js
14 1347 Feb 1 2010 18:06:20 -08:00 gui/Plus.gif
15 843 Feb 1 2010 18:06:20 -08:00 gui/sxiconad.gif
16 174 Feb 1 2010 18:06:20 -08:00 gui/Tab.gif
17 2431 Feb 1 2010 18:06:20 -08:00 gui/telephony_service.html
18 870 Feb 1 2010 18:06:20 -08:00 gui/uparrow.gif
19 9968 Feb 1 2010 18:06:22 -08:00 gui/xml-test.html
20 3412 Feb 1 2010 18:06:22 -08:00 gui/xml.template
21 496521 Feb 1 2010 18:06:26 -08:00 music-on-hold.au
22 0 Feb 1 2010 18:06:26 -08:00 phone
23 0 Feb 1 2010 18:06:26 -08:00 phone/7906-7911
24 0 Feb 1 2010 18:07:08 -08:00 phone/7921
25 0 Feb 1 2010 18:08:18 -08:00 phone/7936
26 0 Feb 1 2010 18:08:32 -08:00 phone/7940-7960
27 0 Feb 1 2010 18:08:42 -08:00 phone/7941-7961
28 42944292 Feb 3 2010 15:43:44 -08:00 c2801-advipservicesk9-mz.124-15.T7.bin
29 2453223 Feb 1 2010 19:10:24 -08:00 apps41.8-2-2ES1.sbn
30 435144 Feb 1 2010 19:10:26 -08:00 cnu41.8-2-2ES1.sbn
31 2141085 Feb 1 2010 19:10:42 -08:00 cvm41sccp.8-2-2ES1.sbn
32 509001 Feb 1 2010 19:10:46 -08:00 dsp41.8-2-2ES1.sbn
33 229364 Feb 1 2010 19:10:48 -08:00 jar41sccp.8-2-2ES1.sbn
34 642 Feb 1 2010 19:10:48 -08:00 SCCP41.8-2-2SR1S.loads
35 642 Feb 1 2010 19:10:48 -08:00 term41.default.loads
36 642 Feb 1 2010 19:10:48 -08:00 term61.default.loads
37 129828 Feb 1 2010 21:23:42 -08:00 P00308000400.bin
• #5 Building the ephones and telephony-service on Redding
To get to the CME GUI on the router you need to set this path:
!
ip http path flash:/gui
As you can see from the flash directory listing above the /gui is where all the files that make the CME web function.
This is a dump of all the files you find in the flash after performing the steps outlines in the "archive" retrieval. That process is documented here:
1. Download the phone load files from CCO. The latest load files will be included in cme-124-15T.zip file or the cme-basic-4.1.0.0.tar file.
For example, if the system is running CME 4.1, you would use cme-basic-4.1.0.0.tar
All cme-basic-x.x.x.x.tar files are posted on the CCO site below:
http://www.cisco.com/cgi-bin/tablebuild.pl/ip-iostsp
2. Extract phone load files to your router flash. Copy the cme-basic-x.x.x.x.tar to a TFTP server,
and enter archive command to extract contents of tar file to router Flash:
For example, if you the TFTP server address is 192.168.1.1, you would enter:
archive tar /xtract tftp://192.168.1.1/cme-basic-4.1.0.0.tar flash:
3. Share the phone load files by issuing the command 'tftp-server flash:Pxxxxxx' for each file on the flash.
TFTP Server statements needed for 7941 7961 phones
archive tar /xtract tftp://x.x.x.x/cmterm-7941_7961-sccp.8-2-2SR1.tar flash:
tftp-server flash:apps41.8-2-2ES1.sbn
tftp-server flash:cnu41.8-2-2ES1.sbn
tftp-server flash:cvm41sccp.8-2-2ES1.sbn
tftp-server flash:dsp41.8-2-2ES1.sbn
tftp-server flash:jar41sccp.8-2-2ES1.sbn
tftp-server flash:SCCP41.8-2-2SR1S.loads
tftp-server flash:term41.default.loads
tftp-server flash:term61.default.loads
telephony-service
load 7941 SCCP41.8-2-2SR1S
load 7961 SCCP41.8-2-2SR1S
____________________________________________________________
TFTP Server statements for 7940 7960 phones
archive tar /xtract tftp://x.x.x.x/P00308000400.tar flash:
tftp-server flash:P00308000400.bin
tftp-server flash:P00308000400.loads
tftp-server flash:P00308000400.sb2
tftp-server flash:P00308000400.sbn
telephony-service
load 7960-7940 P00308000400
4. Specify the load command for each phone type (refer to examples above) - afterwards, configure the command "create-cnf" underneath telephony service.
For CME 4.1, your running configuration will look like this:
telephony-service
load 7960-7940 P00308000400
max-ephones 24
max-dn 24
ip source-address 192.168.1.1 port 2000
max-conferences 12 gain -6
transfer-system full-consult
create cnf-files version-stamp Jan 01 2010 00:00:00
____________________________________________________________
After following all that, this is what mine looks like:
tftp-server flash:apps41.8-2-2ES1.sbn
tftp-server flash:cnu41.8-2-2ES1.sbn
tftp-server flash:cvm41sccp.8-2-2ES1.sbn
tftp-server flash:dsp41.8-2-2ES1.sbn
tftp-server flash:jar41sccp.8-2-2ES1.sbn
tftp-server flash:SCCP41.8-2-2SR1S.loads
tftp-server flash:term41.default.loads
tftp-server flash:term61.default.loads
!!
!
sccp local Loopback0
sccp ccm 162.2.250.250 identifier 1
sccp
!
sccp ccm group 123
associate ccm 1 priority 1
associate profile 1 register IP_7961
keepalive retries 5
switchover method immediate
switchback method immediate
switchback interval 5
!
dspfarm profile 1 transcode
associate application SCCP
shutdown
!
!
dial-peer voice 1 voip
destination-pattern 9.T
session target ipv4:10.255.253.200
incoming called-number .
dtmf-relay h245-alphanumeric
no vad
!
!
telephony-service
load 7961 P00308000400
max-ephones 24
max-dn 24
ip source-address 162.2.245.1 port 2000
time-format 24
date-format dd-mm-yy
max-conferences 8 gain -6
moh music-on-hold.au
multicast moh 239.10.16.4 port 2000
transfer-system full-consult
create cnf-files version-stamp Feb 01 2010 19:20:00
!
!
ephone-dn 1 dual-line
number 43701
label Cisco
description 43701
name Admin Desk
!
!
ephone-dn 2 dual-line
number 43702
label Cisco
description 43702
name Agent Desk
!
!
ephone-dn 12 dual-line
number 4724154
!
!
ephone 1
device-security-mode none
mac-address 001F.9E24.870E
speed-dial 1 43700 label "PAGE ALL PHONES"
paging-dn 11
type 7961
button 1o1,12
!
!
!
ephone 2
device-security-mode none
mac-address 0003.E32A.1DEA
speed-dial 1 43700 label "PAGE ALL PHONES"
paging-dn 11
type 7960
button 1o2,12
• #6 Place an ASA 5500 in transparent mode in between the last hop router named Sacramento and Redding to protect the internal network and the voice traffic coming in.
ASA Version 8.2(1)
!
firewall transparent
hostname dmz-asa
!
interface Ethernet0/0
nameif outside
security-level 0
!
interface Ethernet0/1
nameif inside
security-level 100
!
description Cisco Skinny Client Control Protocol
port-object eq 2000
access-list inside_access_in extended permit ip any any
access-list outside_access_in extended permit tcp any host CME object-group Cisco_SCCP
access-list outside_access_in extended permit udp any host CME eq isakmp
access-list outside_access_in extended permit udp any host CME eq tftp
access-list outside_access_in extended permit icmp any host CME
access-list outside_access_in extended permit icmp any host Laptop
!
ip address 162.2.245.10 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
!
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
!
aaa authentication enable console LOCAL
http server enable
http 162.2.245.0 255.255.255.0 inside
!
#7 Build an IPSec over GRE tunnel to allow secure communication from the phones to the call manager.
Chico Router:
crypto isakmp policy 10
authentication pre-share
!
crypto isakmp key CISCO address 162.2.245.1
!
!
crypto ipsec transform-set TRANS esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile CHICO
set transform-set TRANS
crypto map IPSEC 10 ipsec-isakmp
set peer 162.2.245.1
set transform-set TRANS
match address 101
!
interface Tunnel0
ip address 10.200.1.6 255.255.255.254
tunnel source 192.168.100.1
tunnel destination 162.2.245.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile CHICO
!
access-list 101 permit ip 172.16.100.0 0.0.0.255 host 162.2.245.1
____________________________________________________________
Redding Router:
crypto isakmp policy 10
authentication pre-share
!
crypto isakmp key CISCO address 192.168.100.1
!
!
crypto ipsec transform-set TRANS esp-3des esp-md5-hmac
mode transport
crypto ipsec profile REDDING
set transform-set TRANS
!
crypto map IPSEC 10 ipsec-isakmp
set peer 192.168.100.1
set transform-set TRANS
match address 101
!
interface Tunnel0
ip address 10.200.1.4 255.255.255.254
tunnel source 162.2.245.1
tunnel destination 192.168.100.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile REDDING
!
access-list 101 permit ip host 162.2.245.1 172.16.100.0 0.0.0.255

This design has a bunch of technologies mixed into it so I have laid out the goals and the configuration that supports the design.
• #1 Bring up a 2811 named Chico running Advanced IP Services 12.4(15) T9 and hang a WAN connection off it - using either a static IP, or DHCP given address, both option will be shown.
11 -rw- 51432612 May 22 2009 07:17:46 -07:00 c2800nm-advipservicesk9-mz.124-15.T9.bin
interface FastEthernet0/0
ip address 192.168.100.1 255.255.255.252
duplex auto
speed auto
• #2 Configure DHCP and option 150 on Chico to show the devices (phones) where the Call Manager Express (CME) lives.
ip dhcp pool VOICE
network 172.16.100.0 255.255.255.0
option 150 ip 162.2.245.1
default-router 172.16.100.1
ip dhcp excluded-address 172.16.100.1
• #3 Configure a PoE switch with a voice vlan for the phones to hang off and uplink that to Chico via a trunk.
chico#
interface FastEthernet0/1.2
encapsulation dot1Q 2
ip address 172.16.100.1 255.255.255.0
• #4 Build a WAN between Chico and a 2801 named Redding and load Advanced IP Services 12.4(15) T7 and the appropriate CME files into its flash.
chico#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 192.168.100.0 0.0.0.3 area 1
sacramento#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 10.10.1.4 0.0.0.3 area 0
yolo#
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 10.10.1.4 0.0.0.3 area 0
network 192.168.100.0 0.0.0.3 area 1
redding#
ip route 0.0.0.0 0.0.0.0 FastEthernet0/0
- Files in Redding's Flash. Not sure all this stuff is needed but here's the mess:
1 10035 Feb 1 2010 18:06:10 -08:00 CME41-basic-readme.txt
2 0 Feb 1 2010 18:06:10 -08:00 gui
3 4802 Feb 1 2010 18:06:12 -08:00 gui/admin_user.html
4 657587 Feb 1 2010 18:06:16 -08:00 gui/admin_user.js
5 1602 Feb 1 2010 18:06:16 -08:00 gui/CiscoLogo.gif
6 716 Feb 1 2010 18:06:16 -08:00 gui/CME_GUI_README.TXT
7 953 Feb 1 2010 18:06:16 -08:00 gui/Delete.gif
8 16344 Feb 1 2010 18:06:18 -08:00 gui/dom.js
9 864 Feb 1 2010 18:06:18 -08:00 gui/downarrow.gif
10 6146 Feb 1 2010 18:06:18 -08:00 gui/ephone_admin.html
11 4658 Feb 1 2010 18:06:18 -08:00 gui/logohome.gif
12 3724 Feb 1 2010 18:06:18 -08:00 gui/normal_user.html
13 81443 Feb 1 2010 18:06:20 -08:00 gui/normal_user.js
14 1347 Feb 1 2010 18:06:20 -08:00 gui/Plus.gif
15 843 Feb 1 2010 18:06:20 -08:00 gui/sxiconad.gif
16 174 Feb 1 2010 18:06:20 -08:00 gui/Tab.gif
17 2431 Feb 1 2010 18:06:20 -08:00 gui/telephony_service.html
18 870 Feb 1 2010 18:06:20 -08:00 gui/uparrow.gif
19 9968 Feb 1 2010 18:06:22 -08:00 gui/xml-test.html
20 3412 Feb 1 2010 18:06:22 -08:00 gui/xml.template
21 496521 Feb 1 2010 18:06:26 -08:00 music-on-hold.au
22 0 Feb 1 2010 18:06:26 -08:00 phone
23 0 Feb 1 2010 18:06:26 -08:00 phone/7906-7911
24 0 Feb 1 2010 18:07:08 -08:00 phone/7921
25 0 Feb 1 2010 18:08:18 -08:00 phone/7936
26 0 Feb 1 2010 18:08:32 -08:00 phone/7940-7960
27 0 Feb 1 2010 18:08:42 -08:00 phone/7941-7961
28 42944292 Feb 3 2010 15:43:44 -08:00 c2801-advipservicesk9-mz.124-15.T7.bin
29 2453223 Feb 1 2010 19:10:24 -08:00 apps41.8-2-2ES1.sbn
30 435144 Feb 1 2010 19:10:26 -08:00 cnu41.8-2-2ES1.sbn
31 2141085 Feb 1 2010 19:10:42 -08:00 cvm41sccp.8-2-2ES1.sbn
32 509001 Feb 1 2010 19:10:46 -08:00 dsp41.8-2-2ES1.sbn
33 229364 Feb 1 2010 19:10:48 -08:00 jar41sccp.8-2-2ES1.sbn
34 642 Feb 1 2010 19:10:48 -08:00 SCCP41.8-2-2SR1S.loads
35 642 Feb 1 2010 19:10:48 -08:00 term41.default.loads
36 642 Feb 1 2010 19:10:48 -08:00 term61.default.loads
37 129828 Feb 1 2010 21:23:42 -08:00 P00308000400.bin
• #5 Building the ephones and telephony-service on Redding
To get to the CME GUI on the router you need to set this path:
!
ip http path flash:/gui
As you can see from the flash directory listing above the /gui is where all the files that make the CME web function.
This is a dump of all the files you find in the flash after performing the steps outlines in the "archive" retrieval. That process is documented here:
1. Download the phone load files from CCO. The latest load files will be included in cme-124-15T.zip file or the cme-basic-4.1.0.0.tar file.
For example, if the system is running CME 4.1, you would use cme-basic-4.1.0.0.tar
All cme-basic-x.x.x.x.tar files are posted on the CCO site below:
http://www.cisco.com/cgi-bin/tablebuild.pl/ip-iostsp
2. Extract phone load files to your router flash. Copy the cme-basic-x.x.x.x.tar to a TFTP server,
and enter archive command to extract contents of tar file to router Flash:
For example, if you the TFTP server address is 192.168.1.1, you would enter:
archive tar /xtract tftp://192.168.1.1/cme-basic-4.1.0.0.tar flash:
3. Share the phone load files by issuing the command 'tftp-server flash:Pxxxxxx' for each file on the flash.
TFTP Server statements needed for 7941 7961 phones
archive tar /xtract tftp://x.x.x.x/cmterm-7941_7961-sccp.8-2-2SR1.tar flash:
tftp-server flash:apps41.8-2-2ES1.sbn
tftp-server flash:cnu41.8-2-2ES1.sbn
tftp-server flash:cvm41sccp.8-2-2ES1.sbn
tftp-server flash:dsp41.8-2-2ES1.sbn
tftp-server flash:jar41sccp.8-2-2ES1.sbn
tftp-server flash:SCCP41.8-2-2SR1S.loads
tftp-server flash:term41.default.loads
tftp-server flash:term61.default.loads
telephony-service
load 7941 SCCP41.8-2-2SR1S
load 7961 SCCP41.8-2-2SR1S
____________________________________________________________
TFTP Server statements for 7940 7960 phones
archive tar /xtract tftp://x.x.x.x/P00308000400.tar flash:
tftp-server flash:P00308000400.bin
tftp-server flash:P00308000400.loads
tftp-server flash:P00308000400.sb2
tftp-server flash:P00308000400.sbn
telephony-service
load 7960-7940 P00308000400
4. Specify the load command for each phone type (refer to examples above) - afterwards, configure the command "create-cnf" underneath telephony service.
For CME 4.1, your running configuration will look like this:
telephony-service
load 7960-7940 P00308000400
max-ephones 24
max-dn 24
ip source-address 192.168.1.1 port 2000
max-conferences 12 gain -6
transfer-system full-consult
create cnf-files version-stamp Jan 01 2010 00:00:00
____________________________________________________________
After following all that, this is what mine looks like:
tftp-server flash:apps41.8-2-2ES1.sbn
tftp-server flash:cnu41.8-2-2ES1.sbn
tftp-server flash:cvm41sccp.8-2-2ES1.sbn
tftp-server flash:dsp41.8-2-2ES1.sbn
tftp-server flash:jar41sccp.8-2-2ES1.sbn
tftp-server flash:SCCP41.8-2-2SR1S.loads
tftp-server flash:term41.default.loads
tftp-server flash:term61.default.loads
!!
!
sccp local Loopback0
sccp ccm 162.2.250.250 identifier 1
sccp
!
sccp ccm group 123
associate ccm 1 priority 1
associate profile 1 register IP_7961
keepalive retries 5
switchover method immediate
switchback method immediate
switchback interval 5
!
dspfarm profile 1 transcode
associate application SCCP
shutdown
!
!
dial-peer voice 1 voip
destination-pattern 9.T
session target ipv4:10.255.253.200
incoming called-number .
dtmf-relay h245-alphanumeric
no vad
!
!
telephony-service
load 7961 P00308000400
max-ephones 24
max-dn 24
ip source-address 162.2.245.1 port 2000
time-format 24
date-format dd-mm-yy
max-conferences 8 gain -6
moh music-on-hold.au
multicast moh 239.10.16.4 port 2000
transfer-system full-consult
create cnf-files version-stamp Feb 01 2010 19:20:00
!
!
ephone-dn 1 dual-line
number 43701
label Cisco
description 43701
name Admin Desk
!
!
ephone-dn 2 dual-line
number 43702
label Cisco
description 43702
name Agent Desk
!
!
ephone-dn 12 dual-line
number 4724154
!
!
ephone 1
device-security-mode none
mac-address 001F.9E24.870E
speed-dial 1 43700 label "PAGE ALL PHONES"
paging-dn 11
type 7961
button 1o1,12
!
!
!
ephone 2
device-security-mode none
mac-address 0003.E32A.1DEA
speed-dial 1 43700 label "PAGE ALL PHONES"
paging-dn 11
type 7960
button 1o2,12
• #6 Place an ASA 5500 in transparent mode in between the last hop router named Sacramento and Redding to protect the internal network and the voice traffic coming in.
ASA Version 8.2(1)
!
firewall transparent
hostname dmz-asa
!
interface Ethernet0/0
nameif outside
security-level 0
!
interface Ethernet0/1
nameif inside
security-level 100
!
description Cisco Skinny Client Control Protocol
port-object eq 2000
access-list inside_access_in extended permit ip any any
access-list outside_access_in extended permit tcp any host CME object-group Cisco_SCCP
access-list outside_access_in extended permit udp any host CME eq isakmp
access-list outside_access_in extended permit udp any host CME eq tftp
access-list outside_access_in extended permit icmp any host CME
access-list outside_access_in extended permit icmp any host Laptop
!
ip address 162.2.245.10 255.255.255.0
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
!
access-group inside_access_in in interface inside
access-group outside_access_in in interface outside
!
aaa authentication enable console LOCAL
http server enable
http 162.2.245.0 255.255.255.0 inside
!
#7 Build an IPSec over GRE tunnel to allow secure communication from the phones to the call manager.
Chico Router:
crypto isakmp policy 10
authentication pre-share
!
crypto isakmp key CISCO address 162.2.245.1
!
!
crypto ipsec transform-set TRANS esp-3des esp-md5-hmac
mode transport
!
crypto ipsec profile CHICO
set transform-set TRANS
crypto map IPSEC 10 ipsec-isakmp
set peer 162.2.245.1
set transform-set TRANS
match address 101
!
interface Tunnel0
ip address 10.200.1.6 255.255.255.254
tunnel source 192.168.100.1
tunnel destination 162.2.245.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile CHICO
!
access-list 101 permit ip 172.16.100.0 0.0.0.255 host 162.2.245.1
____________________________________________________________
Redding Router:
crypto isakmp policy 10
authentication pre-share
!
crypto isakmp key CISCO address 192.168.100.1
!
!
crypto ipsec transform-set TRANS esp-3des esp-md5-hmac
mode transport
crypto ipsec profile REDDING
set transform-set TRANS
!
crypto map IPSEC 10 ipsec-isakmp
set peer 192.168.100.1
set transform-set TRANS
match address 101
!
interface Tunnel0
ip address 10.200.1.4 255.255.255.254
tunnel source 162.2.245.1
tunnel destination 192.168.100.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile REDDING
!
access-list 101 permit ip host 162.2.245.1 172.16.100.0 0.0.0.255
Subscribe to:
Posts (Atom)


