!
router ospf 1
log-adjacency-changes
redistribute connected subnets
network 192.168.0.0 0.0.0.255 area 0
The diagram is here:
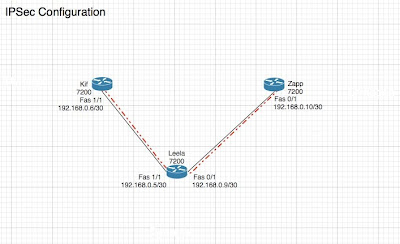
** One thing to note in this, anything that I have defined in the config I have put in upper case lettering. It should be easy to spot things that you need to input as opposed to what is part of the default commands.
• We're going to start with the configuration from Kif and then show you at the end the commands that will be different on Zapp. The first thing we want to do is define the Internet Key Exchange (IKE) Policy. Here we are using Internet Security Association and Key Management Protocol (ISAKAMP) for IKE phase 1 negotiation:
!
crypto isakmp policy 1
- The next part of this configuration specifies the hash and authentication method:
!
hash md5
authentication pre-share
- Now we set the pre shared key and our peer address:
!
crypto isakmp key CISCO address 192.168.0.10
• Now we move onto the transform set which is a mix of security protocols and algorithms:
!
crypto ipsec transform-set DES1 esp-des esp-md5-hmac
- As you can see I put in the "DES1" statement. Thats the name we are using for this transform set. We will see it again later in the configuration.
• Moving onto the crypto map:
!
crypto map DES1_MAP 1 ipsec-isakmp
- Now we set the peer address (same one that we put in the key command above):
!
set peer 192.168.0.10
- Now here is the transform set we defined earlier:
!
set transform-set DES1
- And finally the always confusing match statement. This says anything that matches the ACL we defined (in this case 115) needs to pass through this convoluted configuration we have constructed:
!
match address 115
- Here is ACL 115 so you can see what we have said needs to pass through this:
!
access-list 115 permit ip host 192.168.0.6 host 192.168.0.10
____________________________________________
• Now here are the differences in the config for Zapp:
!
- Crypto address needs to point to the peer
crypto isakmp key cisco address 192.168.0.6 -> this is the IP of Kif's Fastethernet 1/1
- Under crypto map DES1_MAP 1 ipsec-isakmp
set peer 192.168.0.6 -> we know what this is...
!
- ACL needs to be reversed
access-list 115 permit ip host 192.168.0.10 host 192.168.0.6
And thats it! A huge amount of typing and head scratching to make something so simple work. Lets hope we can put this in the time capsule and open it in five years and laugh...

