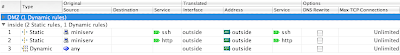
In order to allow generic access (web and ssh) from the outside to your internal network or DMZ you need to do one, possibly two things:
• Configure a policy to permit from a source address or range on a specific port to the network or more preferably a specific host.
• If your outside interface has a DHCP given address, then you will need to build a static NAT rule.
- Lets look at an example
1. We know that we want to allow http and ssh access from the address block 128.107.0.0 through 128.107.255.255 so we will create a network object with that /16 network and define it as "Cisco Registered"
2. We then create an access rule on the outside interface that states from that network object to "any" destination on port 80 (repeated for port 21) we want to permit it.
2a. You can optionally configure a time range for this acl to operate in. Example is 8 to 5 Monday through Friday http requests are allowed....
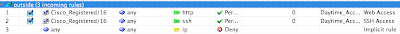
3. Now that you have the access permitted from a specific network into "any" device you need to pick the internal host (all having non routable IP's) and NAT the communication back out.
4. We want to have the http requests come to the web server at 192.168.1.10 so we configure a static NAT rule that says from the inside interface the source is (web server should be defined as a network object and assigned the IP 192.168.1.10) and that is translated to the outside interface using the interface IP (because we have a DHCP given IP and one exit point).
5. In the NAT rule you will want to enable PAT for the original port - 80 translated to port 80.